Private equity firms are snapping up manufacturing companies at a quick pace, setting off a merger and acquisition gold rush, while leaving multi-cloud manufacturing systems unprotected in a Zero Trust world.
Securing the manufacturing gold rush of 2019
The intensity private equity (PE) firms have for acquiring and aggregating manufacturing businesses is creating an abundance of opportunities for cybercriminals to breach the resulting businesses. For example, merging formerly independent infrastructures often leads to manufacturers maintaining — at least initially — multiple identity repositories such as Active Directory (AD), which contain privileged access credentials, usernames, roles, groups, entitlements, and more. Identity repository sprawl ultimately contributes to maintenance headaches but, more importantly, security blind spots that are being exploited by threat actors regularly.
A contributing factor is a fact that private equity firms rarely have advanced cybersecurity expertise or skills and therefore don’t account for these details in their business integration plans. As a result, they often rely on an outdated “trust but verify” approach, with trusted versus untrusted domains and legacy approaches to identity access management.
The speed PE firms are driving the manufacturing gold rush is creating a sense of urgency to stand up new businesses fast – leaving cybersecurity as an afterthought, if even a consideration at all. Here are several insights from PwC’s Global Industrial Manufacturing Deals Insights, Q2 2019 and Private Equity Trend Report, 2019, Powering Through Uncertainty:
- 39% of all PE investors rate the industrial manufacturing sector as the most attractive for acquiring and rolling up companies into new businesses
- The manufacturing industry saw a 31% increase in deal value from Q1 2019 to Q2 2019 with industrial manufacturing megadeals driving deal value to $27.4B in Q2, 2019, on 562 deals
- Year-to-date North American manufacturing has generated 184 deals worth $15.2B in 2019
- Worldwide and North American cross-sector manufacturing deal volumes increased by 32% and 30% in Q2, 2019 alone
PE firms are also capitalising on how many family-run manufacturers are in the midst of a generational change in ownership. Company founders are retiring, and their children, nearly all of whom were raised working on the shop floor, are ready to sell. PE firms need to provide more cybersecurity guidance during these transactions to secure companies in transition. Here’s why:
- According to the 2019 Verizon Data Breach Investigation Report, manufacturing has been experiencing an increase in financially-motivated breaches in the past couple of years, whereby most incidents involve Phishing and the use of stolen credentials
- Manufacturing’s most commonly compromised data includes credentials (49%), internal operations data (41%), and company secrets (36%) according to the 2019 Verizon Data Breach Investigation Report
- 50% of manufacturers report experiencing a data breach or cyber-attack over the last 12 months, 11% of which were severe, according to the Sikich M&D Report 2019
- It’s the smaller suppliers in the supply chain or M&A process that hackers are starting to exploit to bring down many of the world’s largest manufacturing companies. Just ask one of the world’s leading shipping providers, A.P. Møller-Maersk
How to secure multi-cloud manufacturing systems in a Zero Trust world
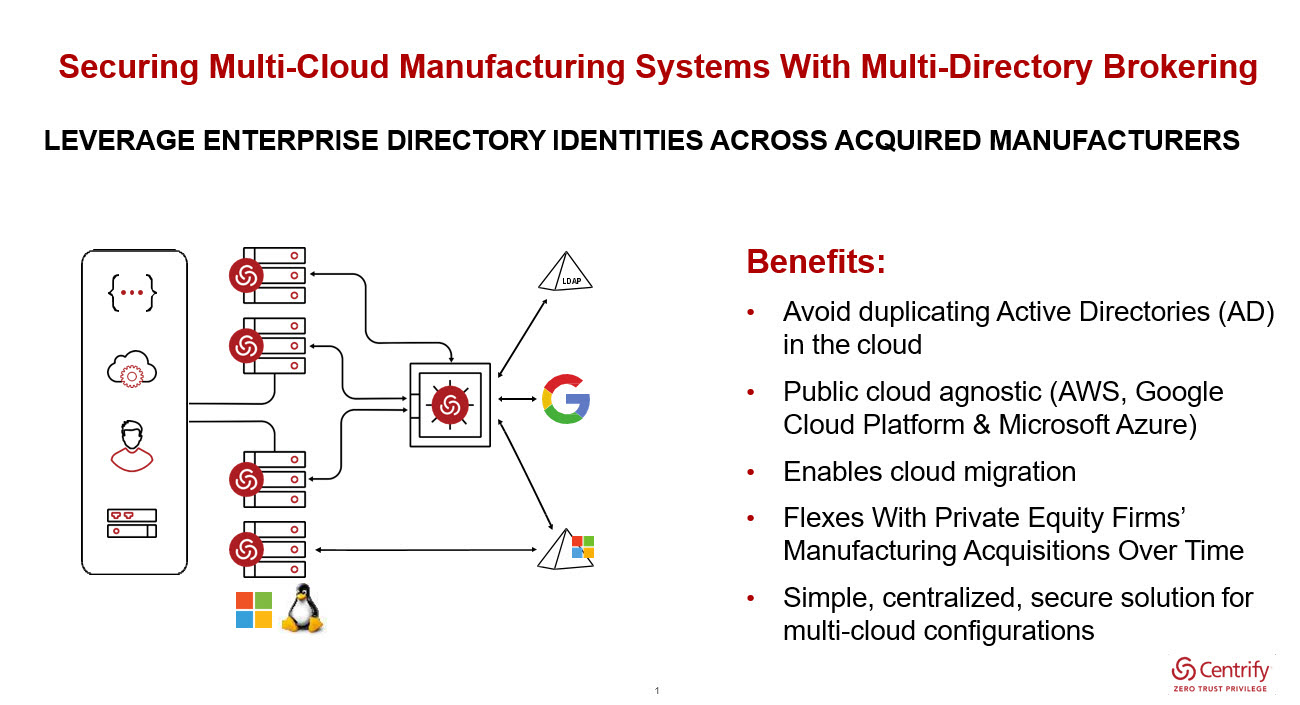
To stop the cybercriminals’ gold rush, merged manufacturing businesses need to take the first step of adopting an approach to secure each acquired company’s identity repositories, whether on-premises or in the cloud. For example, instead of having to reproduce or continue to manage the defined rights and roles for users in each AD, manufacturing conglomerates can better secure their combined businesses using a multi-directory brokering approach.
Multi-directory brokering, such as the solution offered by privileged access management provider Centrify, empowers an organisation to use its existing or preferred identity directory as a single source of truth across the organisation, brokering access based on a single identity rather than having to manage user identities across multiple directories. For example, if an organisation using AD acquires an organisation using a different identity repository or has multiple cloud platforms, it can broker access across the environment no matter where the “master” identity for an individual exists. This is particularly important when it comes to privileged access to critical systems and data, as “identity sprawl” can leave gaping holes to be exploited by bad actors.
Multi-directory brokering is public cloud-agnostic, making it possible to support Windows and Linux instances in one or multiple infrastructure as a service (IaaS) platforms to secure multi-cloud manufacturing systems. The following diagram illustrates how multi-directory brokering scales to support multi-cloud manufacturing systems that often rely on hybrid multi-cloud configurations.
Manufacturers who are the most negatively impacted by the trade wars are redesigning and re-routing their supply chains to eliminate tariffs, so they don‘t have to raise their prices. Multi-cloud manufacturing systems are what they’re relying on to accomplish that. The future of their business will be heavily reliant upon how well they can secure the multi-cloud configurations of their systems. That’s why multi-directory brokering makes so much sense for manufacturers today, especially those looking for an exit strategy with a PE firm.
The PE firms driving the merger and acquisition (M&A) frenzy in specific sectors of manufacturing need to take a closer look at how identity and access management (IAM) is being implemented in the manufacturing conglomerates they are creating. With manufacturing emerging as a hot industry for PE, M&A, and data breaches, it’s time to move beyond replicating Active Directories and legacy approaches to IAM. One of the most important aspects of a successful acquisition is enabling administrators, developers, and operations teams to access systems securely, without massive incremental cost, effort, and complexity.
Conclusion
The manufacturing gold rush for PE firms doesn’t have to be one for cybercriminals as well. PE firms and the manufacturing companies they are snapping up need to pay more attention to cybersecurity during the initial integration phases of combining operations, including how they manage identities and access. Cybercriminals and bad actors both within and outside the merged companies are lying in wait, looking for easy-exploitable gaps to exfiltrate sensitive data for monetary gain, or in an attempt to thwart the new company’s success.
 Interested in hearing industry leaders discuss subjects like this and sharing their experiences and use-cases? Attend the Cyber Security & Cloud Expo World Series with upcoming events in Silicon Valley, London and Amsterdam to learn more.
Interested in hearing industry leaders discuss subjects like this and sharing their experiences and use-cases? Attend the Cyber Security & Cloud Expo World Series with upcoming events in Silicon Valley, London and Amsterdam to learn more.