
Consumers are using technology to their advantage. With it, they are less tolerant, less loyal and more promiscuous. They have learned how to exercise control over brands.
In this kind of environment, it’s important to remember that the success of any customer-facing organisation depends on the experience they deliver. Consumers want meaningful, timely, and personalised engagements, and to gain this, businesses need a single view of the customer and a relationship that goes beyond a single transaction.
New technologies, cloud-native applications and ‘always-on’ connectivity provide the core ingredients companies need to diversify their services and become customer-centric. This demands a truly holistic experience that puts people, not processes, at the forefront of decision making and customer communication.
To operate a connected enterprise, you must tick off the following five considerations:
Have a single view of customers
The consumer is the boss – and can walk away at any time. They determine how they want to interact and demand seamless engagement across any channel. To engage customers, organisations must understand them individually, comprehensively and consistently at any point in time. A complete view of the consumer, across the business, is the only way to extract actionable data that leads to customer retention.
However, in our SAP Customer Data Imperative report, based on a survey of 500 client-side marketers, only 42% of respondents felt they had a consolidated view of first-party data across the enterprise, even though 82% thought it was ‘critical’ or ‘important.’
If marketers are to take ownership of customer data, they must ensure they are building the right connections with other business functions to help work towards a single customer view, including both online and offline data.
Front and back office
To achieve a comprehensive view of each individual customer experience, front-to-back office integration is also essential. This requires a unified front office to orchestrate customer journeys, whilst connecting with the back office to gather insights into customer preference. Knowing what the customer wants, when the customer wants it and being able to deliver it by having in-moment insight to inventory, will create a holistic experience for customers.
To get there, an integrated technology stack is imperative for companies seeking to collate customer data. Yet 41% of respondents cite disparate technology platforms as one of their three biggest challenges in the same Customer Data Imperative report. This is why SAP is connecting back-office capabilities with front office SAP ERP products, providing users an end-to-end experience.
Optimised for machine learning and IoT
In a separate SAP survey, six out of 10 business leaders have implemented, or are planning to implement, AI in the next year. This is because machine learning can analyse data at speed and make predictions that guide the strategy of human teams.
Through machine learning, and combining Internet of Things (IoT) data with insight from other applications, businesses can build a 360-degree customer view which allows an organisation to tailor experiences to customer needs.
Data from supply and demand
A unified supply and demand overview enables companies to better understand, analyse, manage and respond to variability within their supply chains. To do this, businesses must have in place real-time supply chain planning solutions to take advantage of analytics, what-if simulation, alerts and more. This will also help them better respond to ever-developing market expectations so that customers are never left wanting.
Unified cloud
Because today’s buying activity will be done before a human interaction ever takes place, organisations are trying to move siloed CRM systems away from sales and use their data in a way that keeps customers engaged at any point in time.
As such, the success of any business in the digital economy depends on the experiences they deliver. Businesses must therefore view customers holistically, end-to-end and continuously.
By having one unified suite of cloud solutions, businesses can manage customer experiences based on one trusted customer data model, which integrates all of the above. It provides the ability to deliver customer-centric processes and better outcomes, which will in turn build customer trust and loyalty.
The consumer-driven growth revolution will require all businesses to change. By putting together these steps to ensure a connected enterprise, then you can be one step ahead of the competition.
Editor’s note: Find out more about how the connected enterprise can help retain and win more customers at SAP Customer Experience LIVE, from October 10-11 in Barcelona.

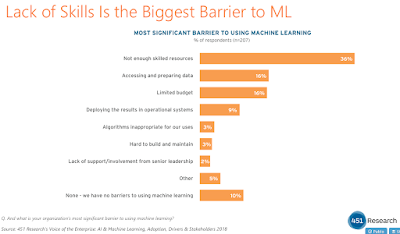
 Interested in finding out more around enterprise AI use cases and how AI and big data will converge? The
Interested in finding out more around enterprise AI use cases and how AI and big data will converge? The 



