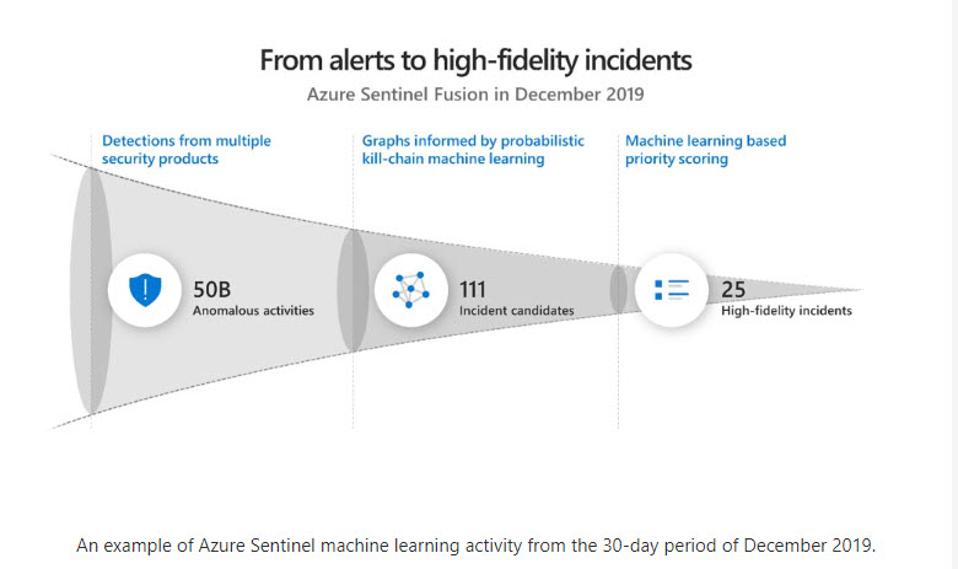
Analysis Cyber risk has overtaken financial risk as the greatest threat that we all face, according to PwC’s 2019 global crisis survey. There are also concerning parallels between the global financial crisis of 2009, and the current cyber threat landscape
The question is, to what extent is cyber insurance the answer?
Currently most companies don’t have any cyber insurance. Coverage is only 40% in the US, and 10% in the UK. Elsewhere, it’s even lower. Many cyber insurers boast that they can provide an insurance quote in under an hour. If they are able to provide cover for such a complex policy in such a short period of time then this should ring alarm bells. You should be concerned with their ability not only to accurately assess your risk position, but also to price the policy accurately.
Some insurers base their risk assessment on cyber security risk ratings. Some of these ratings are produced by firms that use web crawlers that check externally facing endpoints for known vulnerabilities. This is a fairly crude method, but it’s probably still the best way to address the mass market at low cost. The problem is, it’s a bit like evaluating fire-safety risk by looking at a photograph of a building taken from across the street. You can get an idea of the building’s shape and size, but you can’t tell if there’s flammable material inside, or if the building is equipped with fire alarms, or sprinkler systems. A photo like this is better than nothing; but it still provides only a basic, limited idea of the real risk.
The reason that some insurers can probably afford to base premiums on such crude risk metrics is that cyber insurance policies often include a host of provisions and exclusions that in effect make it impossible to claim for almost any incident of any kind. If they want to refuse to pay out, they're probably going to find a way of justifying this. Indeed almost the only reason they would pay out at all is to encourage other clients to sign up.
So if there is a global cyber crisis they may well refuse to pay out on any policies and consider withdrawing from the market entirely.
Examples of common cyber insurance terms or exclusions are as follows:
- Policies tend to only cover 'a hacker who specifically targets you alone'. Unfortunately, cyberattacks are rarely focused on a single victim. Often either the same attack vector is used on many victims in a scattergun approach (phishing attacks) or malware is used that is contagious in nature (WannaCry)
- Policies tend not to cover 'any failure…by a cloud/infrastructure provider…unless you own the hardware and software'. Unfortunately, this would not only exclude almost all cloud use, but also exclude almost anything other than hosted services which exclusively use kit you own
- Policies tend not to cover incidents involving a 'third party…not unduly restricted or financially limited by any term in any of your contracts'. This is meant to ensure that the insurer is able to pursue any third party involved for unlimited damages. Unfortunately, this excludes almost all service providers as they themselves tend to specify some limitation to damages in their contracts, such as damages being limited to the value of the contract. No service providers these days offers unlimited liability
- Policies tend not to cover incidents involving 'any individual hacker within the definition of you'. Unfortunately, this would exclude all insider threats
- Policies tend not to cover 'the use by you of any software or systems that are unsupported by the developer'. This clause rarely specifies that the unsupported software needs to be part of the attack vector, which means that you could be excluded if you had a single instance of something like Windows XP on your technology estate, even if this was not part of the attack at all
- Policies tend not to cover incidents 'attributable to any failure…by the Internet Service Provider (ISP) that hosts your website, unless such infrastructure is under your operational control'. Unfortunately, this would exclude all incidents involving any ISP as it is unheard of for ISP infrastructure to be under your operational control
- Policies tend not to cover 'acts of foreign enemies, terrorism, hostilities or warlike operations (whether war is declared or not)'
- Policies tend not to cover 'any error or omission arising out of the provision of negligent professional advice or design'. Unfortunately, if at any time you have tested or assessed your security (as is required under GDPR), but then failed to implement all the resulting recommendations then your cover could be void. So, if you have had penetration testing or certification audits (for ISO 27001 or PCI say) then you need to address every single recommended revision or recommendation or you risk voiding your cover
- Policies tend not to cover 'anything likely to lead to a claim, loss or other liability under this section, which you knew or ought reasonably to have known about before we agreed to insure you'. This is the pre-existing condition provision. This means that if in any business case that your team make for adopting cyber insurance, you cite potential vulnerabilities as reasons for this adoption, then these very vulnerabilities could then be excluded from any cover
For these reasons we have already seen that some claims are not being paid. For example, several major insurers have declined to pay for damages caused by the NotPetya ransomware attack a few years ago. They say it was a “hostile or warlike action” and therefore not covered.
On top of this other claims have only been paid in part. For example, Norsk Hydro received an insurance payout of $3.6 million. That’s only about 6% of the overall damage that was estimated to be as much as $71 million. It covered the cost of the technical fix, but that was it.
Cyber insurance, while important, simply isn’t a substitute for prevention or for crisis preparedness. You need to have all three.
Here are a few measures to consider:
We need increased adoption of cyber insurance cover, with organisations being far more discerning about the policies they adopt:
- Clients need to understand their risk appetite – you could spend an almost infinite amount on cybersecurity, but you don’t necessarily need to do so
- They need to be far more aware of the exclusions in the policies on offer and to base their choice on the nature of the cover rather than purely on price – there’s no point in paying for a cheap policy that won’t pay out
- They need to choose policies that are appropriate for their business and for their risk position – specialist brokers can help you find a policy that is right for you
- They also need to consider separate specialist incident response cover if this is not included in their cyber insurance policy (most don’t include it) – while an elite team could save you from disaster, the wrong team won’t just fail to fix the problem, they could actually make it worse
What we tend to find is those organisations who have incident response cover tend to call in the experts straight away, while those without it often attempt a DIY fix before calling for help. By the time they do call for help though it’s often too late – the impact and exposure have magnified significantly – and they call in the wrong people, not having time to accurately select the right experts.
Almost worse than a policy that won’t pay out is one that won’t provide top quality incident response. Whether your insurer is footing the bill or you are, here’s what you will really need:
- The technical fix: Get expert help from a specialist security response team to identify and the fix problem(s), and do forensics to diagnose the cause and full scope. Getting an immediate fix to resolve the problem, stem any data loss and recover any systems is essential. Any delay will magnify the impact of the incident and damages incurred
- The legal defence: Seek expert advice in cyber and data law to rapidly develop a legal strategy and a legally defensible narrative based on the forensics. Having the right legal strategy and narrative are both essential to limit legal and regulatory exposure
- The brand defence: Get expert cyber comms support to help your internal and agency teams deal with the added complexity and enhanced comms workload. The standard PR approach to crisis management simply won’t work in a cyber incident and may even make things worse
- Social response: Get top global privacy/security influencers to act as trusted voices to counter misinformation with authority and hysteria with reach and credibility. To counter misinformation and hysteria when your own credibility is at an all-time low, you’ll need the support of authoritative opinion leaders in privacy and security
Part of the reason that you need specialists is the fact that traditional crisis tactics don’t work in a cyber crisis.
In a conventional crisis, you need to understand that with most crises or crimes, the criminals get the blame and the company and customers are seen as victims. The conventional PR tactics in a crisis scenario are to contain any issue until it becomes public and then to show empathy for your customers in order to gain sympathy from the press and general public for both you and the clients. It tends to work well.
A cyber incident is different. You’re likely to be on the back foot: a cyber incident could well be public before you even become aware yourselves. What’s more, cyber incidents aren’t instantaneous: the average breach occurs long before it is detected.
Unfortunately, cybercrime is about the only crime where the victim gets the blame. However much you spent on cybersecurity, the press and public will blame you and not the hackers. You need to be prepared to face the regulators, a hostile press and inevitable hysteria and misinformation. Containment is not possible due to GDPR disclosure obligations and showing empathy won’t gain you any sympathy. It’ll simply put your executives in the firing line.
Crisis preparedness is also critical. Scenario planning and realistic simulation exercises are essential for preparedness, and indeed testing and assessment are mandated under GDPR. So if companies don’t do it, and they then have an incident – the regulatory action will be far harsher.
For companies of any size, it’s probably not a matter of ‘if’ they’ll get hit, but ‘when’. And since the average breach takes more than six months to detect, it may well already have happened.
If ever there was a time to make a case to the board for the need for cyber insurance and crisis preparedness, it is now – with a looming pandemic. The last crisis may have been financial, the current one may be health related, but the chances are that the next one with be a cyber crisis. We all need to be prepared for this.
 Interested in hearing industry leaders discuss subjects like this and sharing their experiences and use-cases? Attend the Cyber Security & Cloud Expo World Series with upcoming events in Silicon Valley, London and Amsterdam to learn more.
Interested in hearing industry leaders discuss subjects like this and sharing their experiences and use-cases? Attend the Cyber Security & Cloud Expo World Series with upcoming events in Silicon Valley, London and Amsterdam to learn more.