
Bottom line: Passwordless authentication, endpoint security, cloud-native SIEM platforms, and new API-based data security technologies were the most interesting tech developments, while keynotes focusing on election security, industrial control systems’ vulnerabilities and the persistent threat of state-sponsored ransomware dominated panel discussion.
This year’s RSA Conference was held February 24 to 28 in San Francisco’s Moscone Center, attracting more than 36,000 attendees, 704 speakers, and 658 exhibitors unified by the theme of the human element in cybersecurity. The conference’s agenda is here, with many session recordings and presentation slides available for download.
Before the conference, RSA published the RSAC 2020 Trend Report (PDF, 13 pp., no opt-in). RSA received 2,400 responses to their call for speakers and based their report on an analysis of all submissions. The 10 trends in the RSAC 2020 Trend Report are based on an analysis of all papers submitted to the conference. It’s a quick read that provides a synopsis of the main themes of the excellent sessions presented at RSAC 2020.
The following are the five most interesting takeaways from the 2020 RSA Conference:
Endpoint security products dominated the show floor, with over 120 vendors promoting their unique solutions
There were over 50 presentations and panels on the many forms of endpoint security as well. Instead of competing for show attendees’ attention on the show floor, Absolute Software took the unique approach of completing a survey during RASC 2020. Absolute’s team was able to interview 100 respondents, with most holding the position of a manager/supervisor or C-level executive.
More than three in four respondents reported their organisations are using endpoint security tools, multi-factor authentication, and employee training and education to protect data, devices, and users. You can review their survey results here.
The number of vendors claiming to have Zero Trust solutions grew 50% this year, from 60 in 2019 to 91 in 2020
There continues to be a lot of hype surrounding Zero Trust, with vendors having mixed results with their product and messaging strategies in this area. A good benchmark to use for evaluating vendors in the Zero Trust market is the Forrester Wave: Zero Trust eXtended Ecosystem Platform Providers, Q4 2019, written by Chase Cunningham and published on October 29, 2019. I’ve summarised the lessons learned in the post, What’s New on the Zero Trust Security Landscape In 2019.
Over 30 vendors claimed to have passwordless authentication that met the current FIDO2 standard
In keeping with the theme of this year’s RSA Conference of Human Element, vendors offering passwordless authentication were out in force. Centrify, Entrust Datacard, HID Global, Idaptive, ImageWare, MobileIron, Thales, and many others promoted their unique approaches to passwordless authentication, leveraging the FIDO2 standard.
FIDO2 is the latest set of specifications from the FIDO Alliance, an industry standards organisation that provides interoperability testing and certification for servers, clients, and authenticators that meet FIDO2 specifications. I’ve written a separate post just on this topic, and you can find it here: Why Your Biometrics Are Your Best Password.
Cloud-based security information and event management (SIEM) systems capable of integrating with third party public cloud platforms reflect the maturity nature of this market
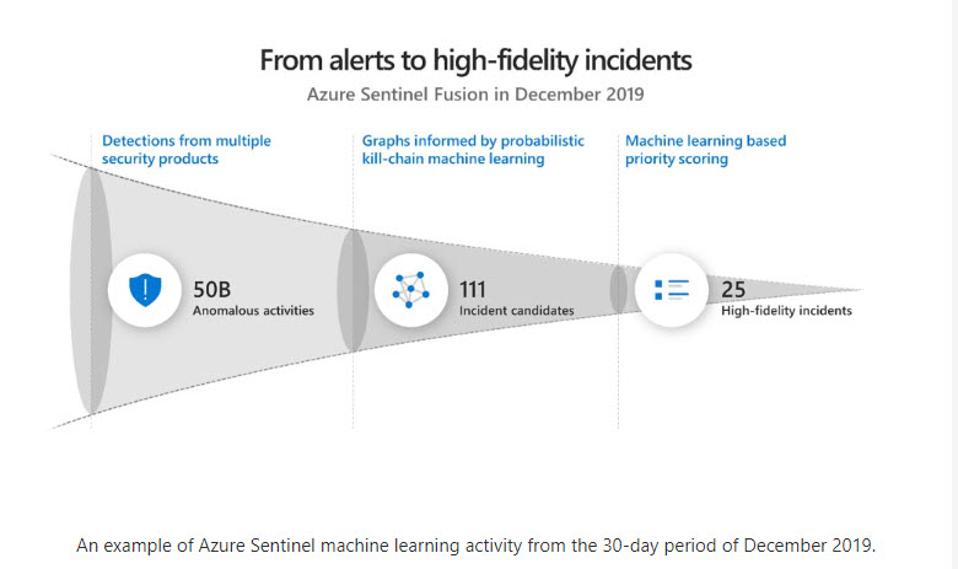
Of the several vendors claiming to have cloud-based SIEM, Microsoft’s Azure Sentinel’s demo showed in real-time how fusion AI technology can parse large volumes of low fidelity signals into a few important incidents for SecOps teams to focus on. Microsoft said that in December 2019 alone, Azure Sentinel evaluated nearly 50 billion suspicious signals, isolating them down to just 25 high-confidence incidents for SecOps teams to investigate. The following graphic explains how Azure Sentinel Fusion works.
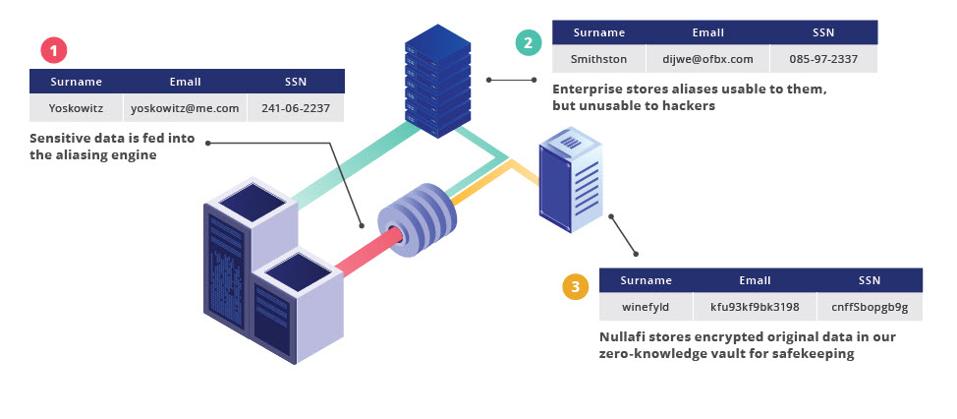
One of the most interesting startups at RSA was Nullafi, who specialises in a novel API-based data security technology that combines data aliasing, vaulting, encryption, and monitoring to create an advanced data protection platform that makes hacked data useless to hackers
What makes Nullafi noteworthy is how they’ve been able to build a data architecture that protects legacy and new infrastructures while making the original data impossible for a hacker to reverse engineer and gain access to. It desensitises critical data so that it’s useless to hackers but still useful for an organisation to keep operating, uninterrupted by a breach to your business. Nullafi is built to AWS GovCloud standards.
The Nullafi SDK encrypts the data before sending it to the Nullafi API. It then re-encrypts the data within their zero-knowledge vault in the cloud (or on-premises). The result is that no sensitive data in any format is shared with Nullafi that could be used or lost, as their architecture doesn’t have visibility into what the actual data looks like. The following graphic explains their architecture:
Main picture credit: Louis Columbus
 Interested in hearing industry leaders discuss subjects like this and sharing their experiences and use-cases? Attend the Cyber Security & Cloud Expo World Series with upcoming events in Silicon Valley, London and Amsterdam to learn more.
Interested in hearing industry leaders discuss subjects like this and sharing their experiences and use-cases? Attend the Cyber Security & Cloud Expo World Series with upcoming events in Silicon Valley, London and Amsterdam to learn more.